Blockchain Technology
Developer’s Guide to Prevent Costly Vulnerabilities with Web3 Security

The future of the decentralized internet, Web3, empowers developers to create decentralized applications (dApps), decentralized finance (DeFi), and many other web3 solutions. However, it also comes with unique risks associated with Web3 security.
Developers need to focus on addressing common Web3 vulnerabilities when building blockchain solutions to prevent potential security risks that could cost millions of dollars in the long run.
This guide will take you on a journey from understanding the basics of Web3 security to exploring common Web3 security issues and best practices to prevent them.
What is Web3?
Before we dive deeper into Web3 security, let’s first understand Web3 itself. Web3, often called the web 3.0, decentralized or semantic web, represents the next stage in the evolution of the internet. It leverages decentralized and peer-to-peer technologies to facilitate secure, trustless interactions while enhancing privacy.
Web3 is built on the foundation of blockchain technology, primarily known for its decentralized nature. It uses a distributed ledger shared across a computer network, allowing greater transparency, security, and privacy.
Web3 has been under development for years and has now reached the point where it can provide complete control over digital assets, including currency, personal data, and digital identities, to users via decentralized applications (dApps), decentralized identity, and decentralized finance (DeFi).
Despite the technological advancements, including trustless systems and strong encryptions, Web3 is not immune to security vulnerabilities or breaches.
What Is Web3 Security?
Web3 security is nothing new; it’s an essential step in the Web3 development process that requires attention to avoid security issues or vulnerabilities. It’s similar to web security, where developers need to test and audit their projects for potential vulnerabilities to prevent data breaches.
Web3 security is about following a set of best practices and protocols when developing Web3 solutions to ensure data is never altered or removed without agreement from the supporting network. This protects sensitive information and financial transactions while ensuring the integrity of decentralized systems.
Web3 Security Architecture
Web3 facilitates the creation of user-generated content while enabling seamless integration with social networks and other communication protocols. This supports the development of accessible applications across various devices and systems.
Meanwhile, Web3 Security Architecture enhances trust, privacy, and security through decentralized mechanisms. It addresses vulnerabilities inherent in traditional centralized systems by leveraging advanced technologies and frameworks.
The architecture also integrates advanced monitoring and analytics for threat detection and auditability, ensuring transparency without compromising security. While Web3 offers a more secure and resilient framework, it requires ongoing development to address challenges like scalability, interoperability, and new attack vectors.
Key components include:
- Blockchain-based data storage, which ensures immutability and transparency;
- Cryptographic techniques like public-key infrastructure (PKI) and zero-knowledge proofs (ZKPs) for secure transactions and data privacy;
- Decentralized identity systems enable users to control their data through self-sovereign identities.
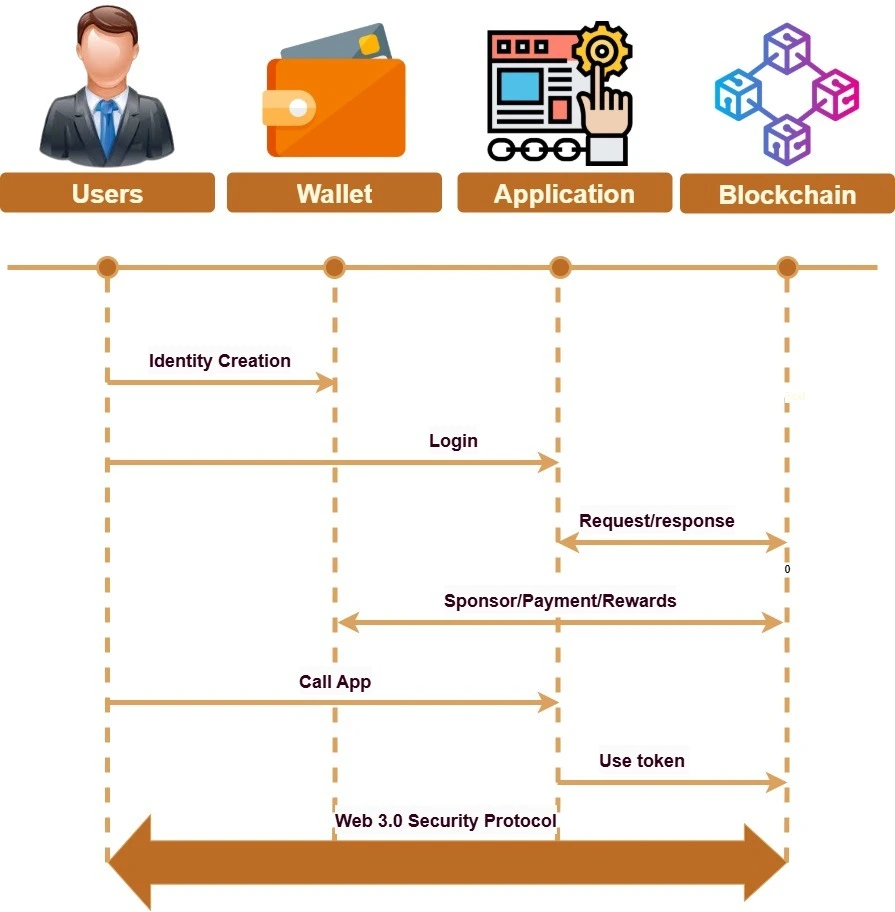
Web3 Vulnerabilities and How Developers Can Prevent Them
Security in Web3 directly depends on blockchain technology, which revolves around two central concepts, decentralization, and strong encryption, which are native features of blockchain. However, the question “Is Web3 really more secure than Web2?” arises due to recent incidents of cyberattacks and breaches.
The direct answer to this question is: Yes, Web3 is more secure than Web2. The explanation lies in the fact that most Web3 security issues are not directly related to the functioning of the blockchain itself. Instead, the majority of them occur at the application layer or during the development process.
Let’s understand the most common Web3 vulnerabilities and how developers can prevent them via a secure development process.
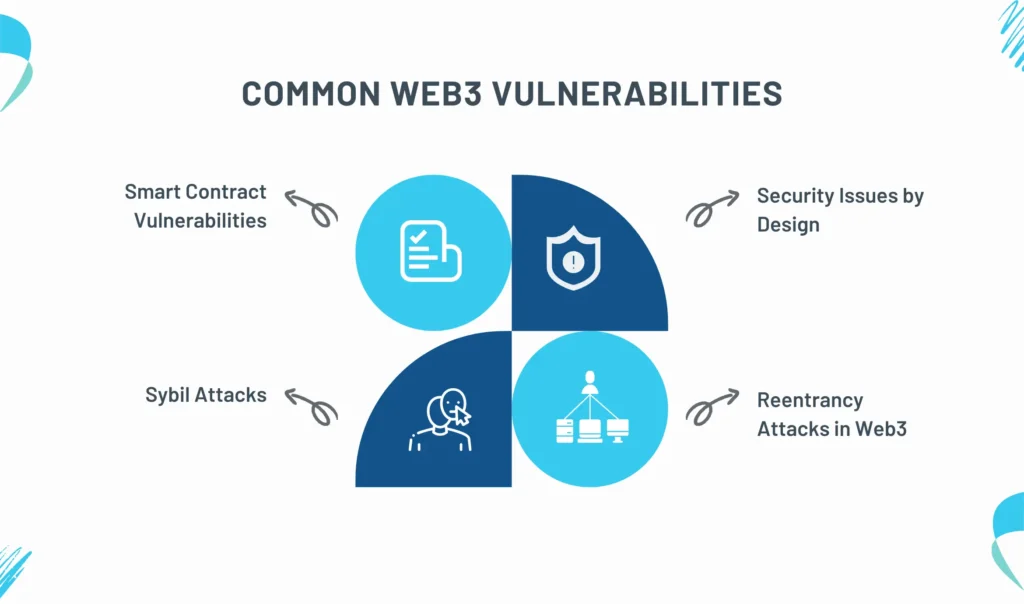
1. Smart Contract Vulnerabilities
Smart contracts are self-executing programs that run on blockchain networks. They are written in programming languages such as Solidity or Vyper. Compared to other well-known programming languages, such as JavaScript and Python, these languages are still under development and come with an immature ecosystem.
While smart contracts enable communication with decentralized systems, they are prone to vulnerabilities due to logical, structural, or testing issues, which hackers can exploit to manipulate operations.
For example:
- Logical errors that allow attackers to bypass contract restrictions.
- Improper input validation leads to overflows or underflows.
- Use of external dependencies that are not well-maintained and updated in time for security patches.
Best Practices to follow:
- Code Audits: Perform code audits to review the smart contract’s code for potential vulnerabilities, such as logical or structural issues.
- Proper Testing: Before deploying the smart contracts, test them using proper security practices for all edges and cases.
- Secure Dependencies: Always rely on trusted external dependencies that are properly maintained.
2. Security Issues by Design
In the race to stay ahead in the Web3 world, companies are developing different solutions for the same problem, many of which are brand new and have not been tested in real-world environments.
Sometimes, as developers focus on creating specific system designs or architectures for Web3 applications to solve particular problems, they underestimate security, leading to poorly designed systems that open up numerous ways for hackers to exploit.
Best Practices to follow:
- Follow Security-First Principles: Design systems with a security-first approach by following secure coding practices rather than focusing solely on output.
- Implement Proper Access Controls: Use role-based security controls to limit the functionality of different system components.
- Stay Aware of Top Vulnerabilities: Developers should build an understanding of the top vulnerabilities to avoid, and apply this knowledge during coding and system development.
- Seek Peer Reviews: Always conduct peer reviews during the development of system designs to identify issues from different developers’ perspectives.
3. Sybil Attacks
Sybil attacks refer to attackers creating multiple fake nodes or identities to influence consensus mechanisms or manipulate decentralized governance systems.
Web3 is particularly vulnerable to Sybil attacks because trust and validation are distributed across numerous nodes in Web3, and if an attacker can introduce a large number of malicious nodes, they can disrupt the consensus process.
Best Practices to follow:
- Implement Identity Validation: Implement decentralized identity protocols, such as DID (Decentralized Identifiers), for identity validation to prevent Sybil attacks.
- Set Up a Hierarchical System: New nodes or identities are likely to be Sybil nodes. To prevent this, assign higher voting power or decision-making authority to nodes that have been in the network for a long time.
- Implement PoW or PoS: Utilizing these consensus mechanisms makes it economically costly for attackers to create multiple fake identities.
4. Reentrancy Attacks in Web3
A reentrancy attack is a Web3 vulnerability where an attacker exploits a flaw in smart contract code by calling the original contract with a malicious contract that makes a recursive call back to the original contract before the first execution is complete. This can lead to unexpected behaviors such as draining funds or manipulating the state.
For example, in the DAO hack, attackers took advantage of the reentrancy vulnerability to withdraw more money than they were entitled to.
Best Practices to follow:
- Limit External Calls: Developers should minimize or completely avoid external contract calls, or properly manage the control flow within their smart contracts.
- Use Reentrancy Guards or Mutex: Implement reentrancy guards or mutex locks to prevent concurrent calls to a function.
- Follow the CEI Pattern: Always follow the CEI (Checks, Effects, and Interactions) to validate conditions, and manage state changes and interactions involving transactions between functions or contracts.
Conclusion
Blockchain comes with strong native security implementation. However, building Web3 applications on the blockchain sometimes leads to Web3 security issues due to developers neglecting to follow proper security guidelines or testers being unable to identify small edge cases, which ultimately leads to bigger cyberattacks.
As a developer, you should be well aware of common Web3 vulnerabilities and how to prevent them by developing more secure Web3 applications and following all necessary security measures.
